Top 5 IoT Security Risks and How to Avoid Them

The Internet of Things (IoT) encompasses a rapidly growing subset of digital products ranging from voice assistants for the home such as Amazon Alexa to wearables like the Apple Watch. IoT products are making every aspect of life smoother, simpler, and more enjoyable, from fitness and entertainment to home security.
As IoT develops at a rapid pace, innovative applications continue to emerge that hold valuable potential for both the B2B and B2C market. Forbes predicts that global spend on IoT will reach $1.2T in 2022. Companies across every sector are rushing to capitalize on this growing trend.
Since immediacy is one of the best benefits IoT technology provides, user experience and actionable outcomes often take center stage during new product development. As frequently as it’s overlooked, though, security is a critical concern that developers and consumers alike serve to gain from prioritizing in both production and consumption.
Based on our thorough research of the state of IoT security, we’ve identified a shortlist of the five most prevalent security problems developers, businesses, and buyers alike should keep in mind when investing in, creating, or purchasing a new connected device.
Our quick problem-and-solution guide pairs common pitfalls with proven solutions to help you navigate the ins and outs of this dynamic field of emerging technology.
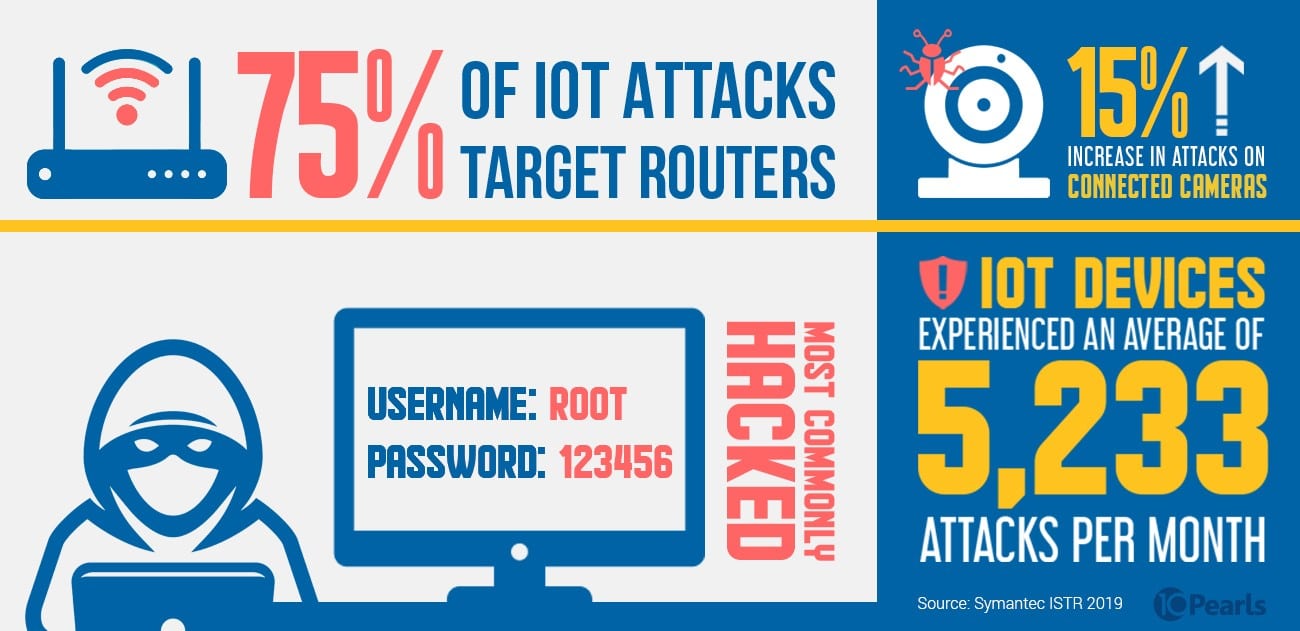 IoT Security Statistics (Source: Symantec ISTR 2019)
IoT Security Statistics (Source: Symantec ISTR 2019)
IoT Security Challenges: With Great Connectivity Comes Great Responsibility
1. Default Logins are an Easy Fix to Secure IoT Devices
Devices that require users to log in to access data are often deployed from the manufacturer and shipped to customers with easy-to-guess, default settings. Businesses can help customers have a better and more secure user experience by including instructions for one simple yet critical first step: changing the username and password before starting to use the new product.
The most commonly hacked logins are listed below:
Generic Usernames:
- Admin
- Root
- User
Default Passwords:
- “Password”
- “123456”
- Worst of all, a blank password
While it might seem obvious from the enterprise perspective, not all buyers realize they need to create unique credentials. Highlighting the importance of customizing the login for their new IoT purchase keeps user data safe while also positioning your brand a cut above the competition as you demonstrate a commitment to security.
2. Limited IoT Processing Power Means Limited Functionality for Security

IoT devices simplify daily tasks and track data from our daily life more accurately with minimal manual effort required. Take our health, for example: complex biometric features like fingerprint scanners, sensors, and haptics enable IoT products to monitor activity level, heart rate, and even sleep quality.
Having these health insights constantly accessible right on our phones helps make wellness a conscious priority. There’s just one major downside: the personal medical data these tracking systems contain can pose a major risk to users if compromised.
Even though the software we use to access daily health data can collect, analyze, and store such a high volume and constant influx of data, the actual IoT hardware these mobile apps connect to and pull metrics from tend to have considerably less processing power.
Additionally, many IoT devices lack the internal resources and computing power necessary for advanced security measures like encryption and two-factor authentication.
Our team at 10Pearls works on the frontlines of R&D to find innovative healthcare security solutions by integrating other forms of emerging technology, such as blockchain.
3. Infrequent IoT Device Updates Compromises Secure and Reliable Use
While the computers and smartphones we use every day send us consistent software update reminders, IoT devices can’t receive such frequent fixes to patch security vulnerabilities. Updating the software that powers IoT hardware tends to take the backseat to other priorities.
Accounting for every possible worst-case scenario can make successful product development feel daunting to achieve. Fortunately, taking a security-first approach is an actionable approach that will yield exponential returns. As you iterate on new releases, make sure you’re investing in continuous security with each new version of your IoT product.
4. Centralized Storage for IoT Software Amplifies Security Risks
Data between IoT devices is stored and authenticated centrally in cloud storage. If a hacker manages to breach the network through a connected device, all the data it contains is easily accessed to malicious parties in its entirety.
From personal health data to home access in lieu of a traditional key, all the valuable assets IoT devices can access make investing in security non-negotiable.
![]() 90% of IoT attacks center on two of the most common devices: routers and connected cameras.
90% of IoT attacks center on two of the most common devices: routers and connected cameras.
As the number of smart devices equipped with internet connectivity grows into the billions, it’s increasingly important to acknowledge the downsides that come along with these groundbreaking new products. Take preemptive measures to offset potential risk factors by choosing a more secure hosting option.
5. Lack of IoT-Specific Industry Standards Poses A Struggle for Security Professionals
No single framework or set of requirements for IoT device security exists as an accepted market standard in 2019. Without set guidelines or regulations, training IT professionals to acquire the right skill set to facilitate IoT security properly can be nearly impossible.

Many of the widespread security vulnerabilities IoT devices commonly experience are largely preventable if the proper steps toward basic security are taken. Which of the points in this overview apply to your business operations, products, or services? Once you identify the relevant actions to take, prioritize quick wins and put a process in place for continuous improvement that emphasizes security.
An Investment in IoT Security is an Investment in the Future
IoT has no limit in sight when it comes to driving acceleration, modernization, and growth for businesses and society alike.
Consider the prediction a recent Forbes article lays out:
With 5G coming fast, IoT innovations are set to change many aspects of society and daily life — opening new markets and opportunities for businesses and entrepreneurs. Self-driving cars and smart roadways are only a few years away. Advanced factory automation, remote monitoring of municipal utilities and telemedicine are also expected to emerge.
Curious about how you stand to benefit from investing in a new IoT product offering? Our team has the expertise and agility to provide turnkey solutions paired with best-in-class continuous security that empowers companies across every industry vertical to protect user data. Watch our CSO Peter Hesse’s video on his tips for designing secure IoT devices.
Keep your business at the forefront of innovation by partnering with 10Pearls for seamless end-to-end product development that embraces security-first.